Poland attributes espionage campaign to Russia-linked APT29
APT29, also known as Cozy Bear, the Dukes, and Nobelium, is reportedly part of the Russian government’s Foreign Intelligence Service (SVR).

The Polish government has warned of a cyber-espionage campaign aimed at collecting information from foreign ministries and diplomatic entities of NATO member states, the EU countries and Africa.
Poland’s Military Counterintelligence Service and its Computer Emergency Response Team have attributed the attacks to Russia-linked advanced persistent threat APT29, also known as Cozy Bear, The Dukes, CozyDuke, Nobelium, and YTTRIUM.
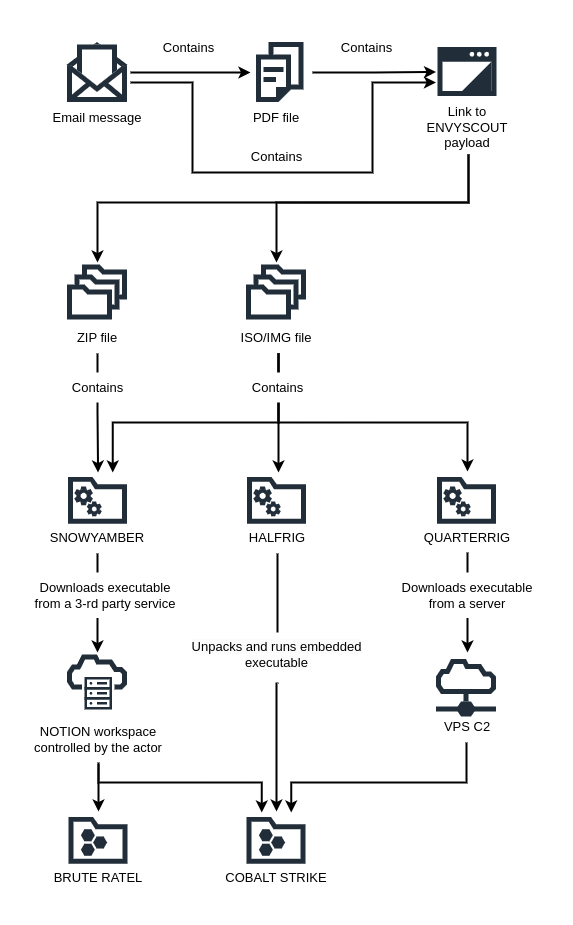
The hackers utilised spear phishing techniques, sending emails impersonating embassies of European countries to selected personnel at diplomatic posts. The emails contained a link which directed to a compromised website, which loaded a malicious HTML document called EnvyScout, the group’s signature HTLM smuggling technique. (In such a technique, when a target user opens the HTML in their web browser, the browser decodes the malicious script, which is then downloaded on the victim’s device.)
In this campaign, APT29 deployed three different versions of the ENVYSCOUT tool. SNOWYAMBER, HALFRIG and QUARTERRIG. SNOWYAMBER and QUARTERRIG sent user data to the attacker. If the attacked determined that the user was of interest to the attacker, SNOWYAMBER and QUARTERRIG would deploy COBALT STRIKE or BRUTE RATEL on the user’s computer. HALFRIG, on the other hand, would run COBALT STRIKE on the user’s computer automatically.
APT29 has been linked to several high-profile cyberattacks, including the 2016 hack of the Democratic National Committee (DNC) in the United States ahead of US presidential elections, targeting organisations involved in COVID-19 vaccine development and research, and Solar Winds supply chain compromise.

